Moving Cloud Users from SAP BTP to On-Premise Systems
Struggling with SAP BTP authentication or setting up Single Sign-On (SSO) using Microsoft Entra ID? You’re not alone. Authentication setup in SAP BTP can be complex, especially when combining SAP Cloud Identity […]
Struggling with SAP BTP authentication or setting up Single Sign-On (SSO) using Microsoft Entra ID? You’re not alone. Authentication setup in SAP BTP can be complex, especially when combining SAP Cloud Identity Services (IAS) with corporate identity providers like Microsoft Entra ID. This article is here to help you get through the tricky parts of authentication setup in SAP BTP without getting lost in complex documentation.
Everything shared here is based on real-world experience. This is not a step-by-step guide. Instead, it is a practical collection of tips and insights to help you avoid common mistakes and save time.
SAP BTP Authentication Tips
• Know the two types of users in SAP BTP:
o Platform users (admins, developers, operators) manage access and services at the global, directory and subaccount level.
o Business users are your end users who access applications such as Fiori apps.
• Custom Identity Provider setup for platform and business users:
o SAP recommends using SAP Cloud Identity Services (IAS) as the identity provider. Here you can connect IAS to your corporate IdP (e.g., Microsoft Entra ID).
o Trust configuration must be done at the global account level. Once set, the custom identity provider (e.g., IAS) applies automatically to all directories, subaccounts, and Cloud Foundry environments. This may take time in larger landscapes. The Default Identity Provider remains required as a fallback and cannot be removed.
o For Business Users, the trust configuration should be set for every subaccount.
o To provide a smoother login experience, you can hide the default identity provider (SAP ID service) by unchecking the “Available for User Logon” checkbox in the Trust Configuration of your subaccount in the SAP BTP Cockpit.
• Before starting Microsoft Entra SSO integration with IAS, make sure you have:
o Access to the Azure Portal with right permissions: Global Administrator, Application Administrator or Cloud Application Administrator.
o Access to the IAS Admin Console.
o Admin access to your SAP BTP landscape.
• Setting Entra ID as a Corporate Identity Provider
o In the SAP Cloud Identity Services Admin Console, navigate to Identity Providers → Corporate Identity Providers.
o Click Create, provide a display name and select Microsoft ADFS / Entra ID as the identity provider type.
• IAS Settings Options
o Once you have successfully configured Entra ID as a corporate identity provider, you may want to avoid managing users manually in SAP Cloud Identity Services. To do this, open the SAP Cloud Identity Services Admin Console. Navigate to Identity Providers → Corporate Identity Providers, select your Entra ID configuration, and go to the Identity Federation section. Enable the option Use Identity Authentication user store.
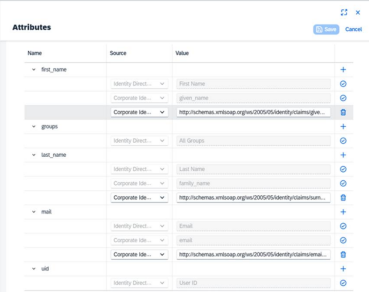
o Then open Single Sign-On section, open Attributes and adjust the attribute mapping configuration to match the user information passed from your corporate IdP:
Note: This is just an example configuration. Always use only the attributes provided by your corporate IdP. Make sure the values match what your applications in SAP BTP expect, especially fields like email, uid, or userName.
• You can forward all SSO requests to Corporate IdP
The Forward All SSO Requests to Corporate IdP option enables your corporate identity provider to handle all single sign-on (SSO) requests when Identity Authentication is used as a proxy. By default, this option is turned off.
o When disabled: IAS might reuse active session.
o When enabled: each app login triggers a fresh SSO flow to Microsoft Entra.
o Choose based on your security expectations and requirements.
• OpenID Connect Trust with SAP Cloud Identity Services
o You can migrate from SAML to OpenID Connect using the SAP BTP command line interface (CLI).
o It is strongly recommended to practice the migration procedure in a development or test subaccount before applying it to your production subaccounts.
o Practicing helps you understand the process, reduces the risk of misconfiguration and minimizes potential downtime in your production environment
• Group-based access with Entra ID:
o You can use Microsoft Entra security groups.
o Map group Object IDs in IAS and connect them to BTP role collections.
o This avoids assigning roles manually in BTP.
• Default Identity Provider in SAP BTP subaccounts with SAP Build Workzone subscription
o For subaccounts using an SAP Build Work Zone subscription, it is recommended to deactivate the Default Identity Provider (sap.default), as proper access requires an identity setup involving SAP Cloud Identity Services, Identity Authentication (IAS) and SAP Cloud Identity Services, Identity Provisioning (IPS).
Useful Official Guides
If you’re looking for detailed, step-by-step instructions from official sources, here are some recommended links that complement the tips in this article:
• Microsoft Entra ID integration with SAP BTP:
Set up SSO using Microsoft Entra ID for SAP BTP (Cloud Foundry)
This tutorial from Microsoft walks you through all steps to configure and test Microsoft Entra SSO for SAP BTP.
• Trust Configuration in SAP BTP:
SAP Discovery Center Mission: Establish Trust Between Global Account and Subaccount
A guided mission that explains how to set up and manage trust configurations across your BTP global account and subaccounts using IAS.
• Managing Access to SAP BTP:
Identity and Access Management with Microsoft Entra – Part I: Managing Access
This SAP Community blog post describes how to manage access in SAP BTP using
Microsoft Entra ID, including user and group setup, and role collection assignments